Securing Ai Agents Prisma Airs Mcp
Securing the Future of AI Agents: How Prisma AIRS Transforms MCP Security
Disclaimer: The author was employed by Palo Alto Networks at the time of this writing. This content does not constitute official communications from Palo Alto Networks and represents the personal views and analysis of the author posted on their individual website.
As AI agents evolve from simple chatbots to sophisticated autonomous systems capable of executing complex workflows, the Model Context Protocol (MCP) has emerged as the semi-de facto standard for AI-tool communication. However, with great capability comes great vulnerability. Today, we’re diving deep into how Palo Alto Networks’ Prisma AIRS is revolutionizing security for MCP-based AI systems.
The MCP Security Challenge: Why Traditional Security Falls Short
Model Context Protocol is a paradigm shifter when it comes to how AI systems invoke external tools and data sources. It deviates from the predictable pattern of requests in traditional API designs, with a dynamic, context-based tool invocation that can string operations together across diverse systems. It is so flexible and so powerful that it introduces new attack vectors that traditional security measures simply aren’t capable of handling.
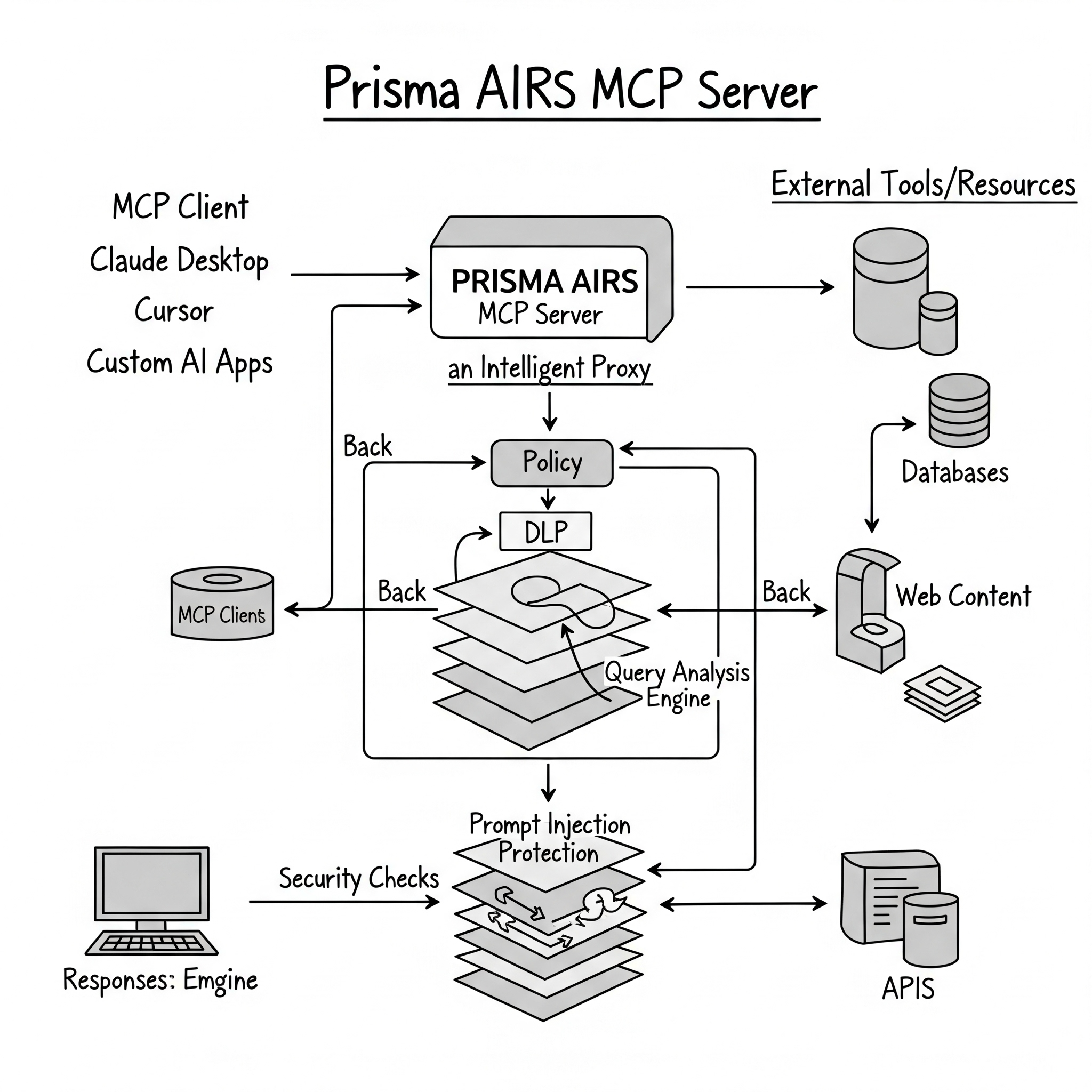
Envision a typical MCP flow: a user request is sent to an AI agent, who determines that it needs to get to a database, fetch web pages, and operate on files—all within milliseconds. Each call to a tool has possible perils: prompt injection attacks, data exfiltration, and privilege escalation threats. Legacy WAFs and API gateways only see slices of this carefully choreographed behavior, not the forest for the trees.
Enter Prisma AIRS: Purpose-Built Security for the AI Era
Palo Alto Networks recognized this shortcoming early and created Prisma AIRS (AI Runtime Security) exclusively for the unique requirements of AI workloads. The Prisma AIRS MCP Server, currently available in public preview, is a quantum leap in AI security architecture.
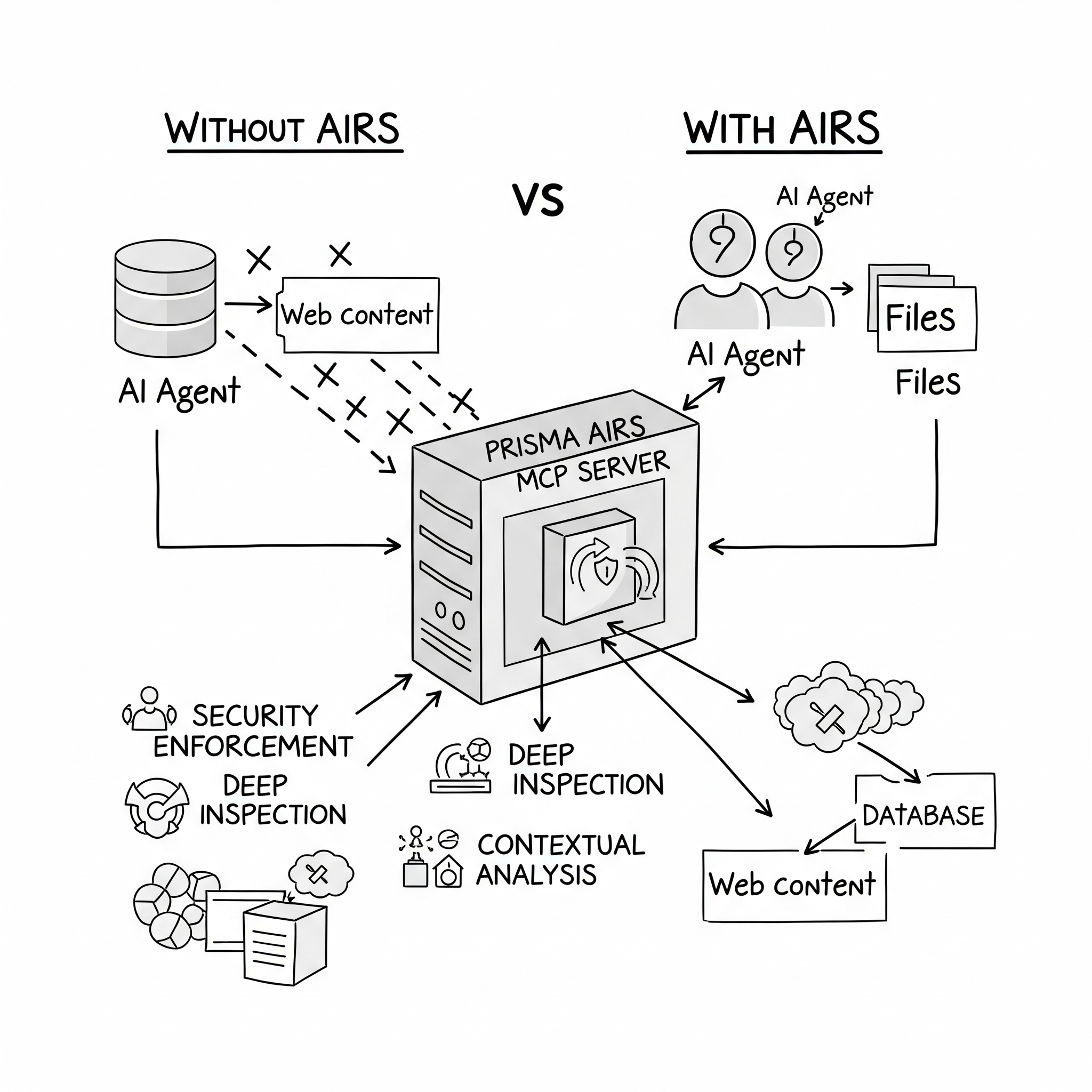
Architectural Innovation: The Security Proxy Pattern
At its core, Prisma AIRS MCP Server includes a smart proxy design that sits between MCP clients (like Claude Desktop, Cursor, or custom AI apps) and the tools they invoke. It’s not yet another layer of middleware—this is a purpose-built security fabric tuned to the semantics of AI communication.
# Example: Prisma AIRS MCP Server initialization
from prisma_airs_mcp import SecurityServer, PolicyEngine
server = SecurityServer(
api_key=os.environ['PRISMA_API_KEY'],
policy_engine=PolicyEngine(
dlp_enabled=True,
toxicity_detection=True,
prompt_injection_protection=True
)
)
# Seamless integration with existing MCP infrastructure
server.register_tool("database_query",
handler=secure_db_handler,
policies=["pii_protection", "sql_injection_prevention"])
The elegance lies in its transparency—developers write standard MCP tool definitions while Prisma AIRS provides comprehensive security enforcement without code modifications.
Deep Inspection: Understanding AI Intent
Unlike traditional security solutions that operate on static rules, Prisma AIRS employs contextual analysis to understand the intent behind AI operations. When an agent attempts to execute a database query, Prisma AIRS doesn’t just scan for SQL injection patterns—it analyzes:
- Semantic context: Is this query consistent with the conversation flow?
- Behavioral patterns: Does this match the agent’s typical access patterns?
- Data sensitivity: What type of information is being accessed?
- Chained operations: How does this fit into the broader workflow?
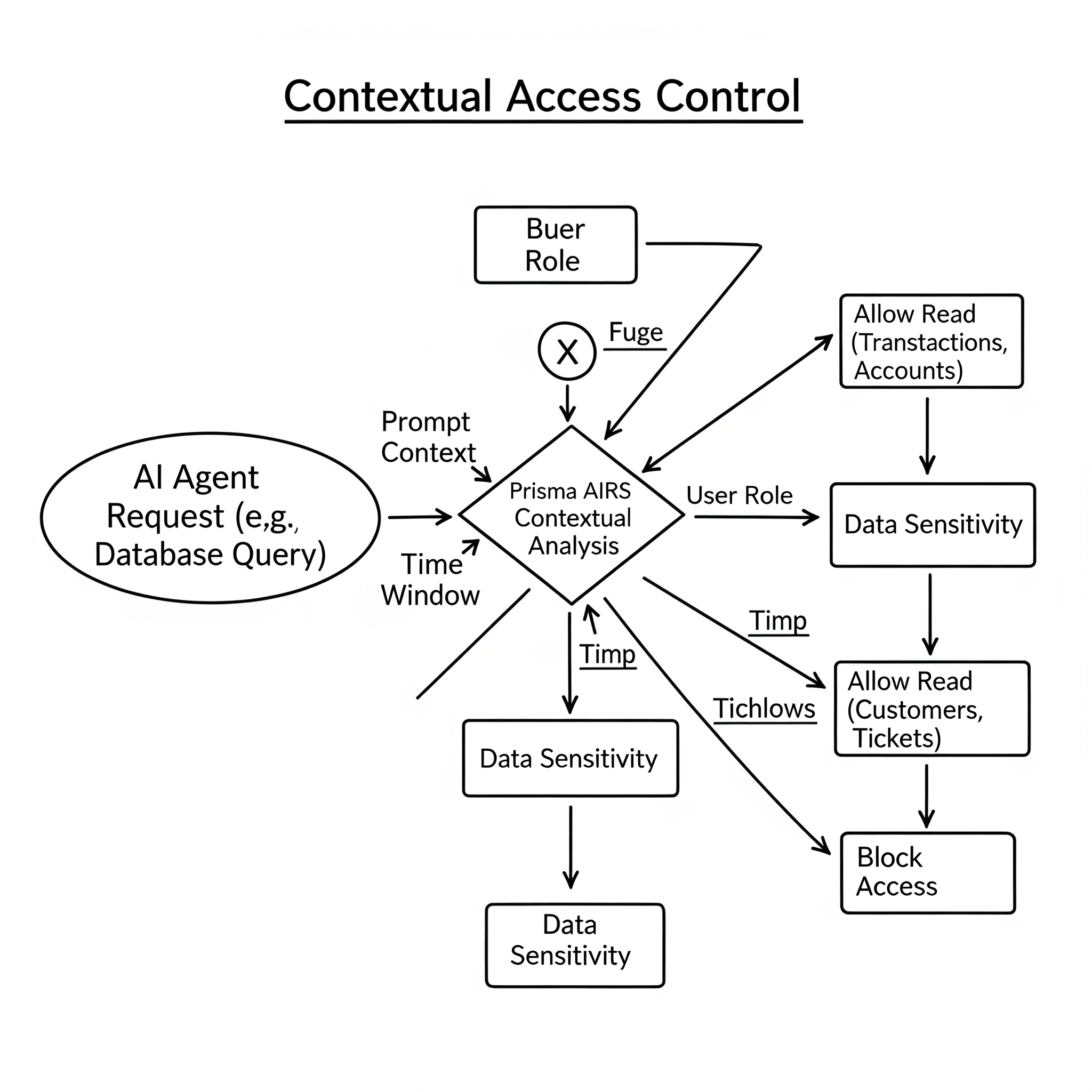
This multi-dimensional analysis enables detection of sophisticated attacks that would bypass traditional security layers.
Technical Deep Dive: Core Capabilities
1. Advanced Prompt Injection Defense
Prisma AIRS protects against 29+ distinct types of prompt injection attacks in 8 languages. The product employs a multi-layered defense strategy:
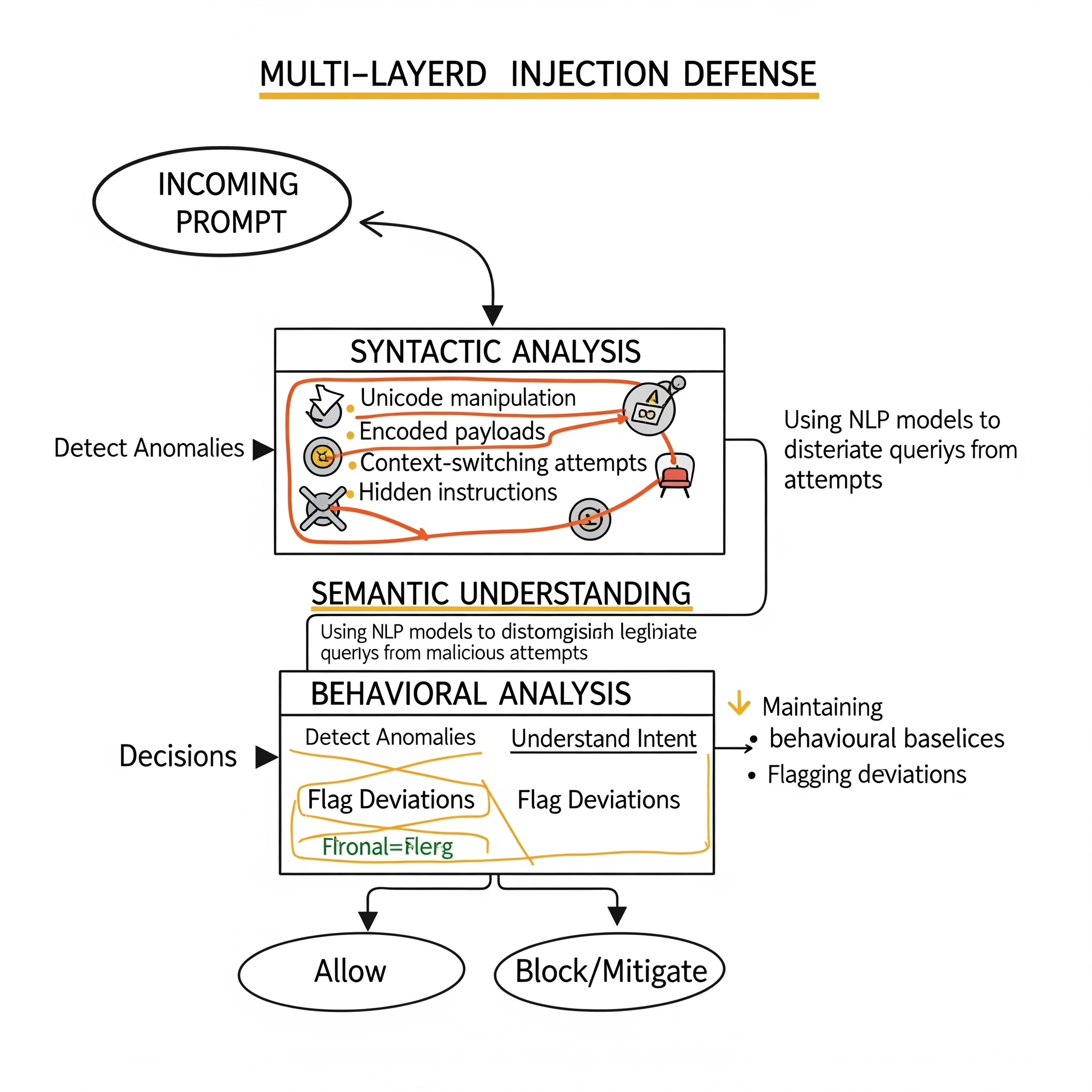
- Layer 1: Syntactic Analysis
The engine performs live parsing of prompts in real-time to identify structural anomalies typical of injection attempts. This includes:
- Unicode manipulation techniques
- Encoded payloads
- Context-switching attempts
- Hidden commands in various forms
-
Layer 2: Semantic Interpretation Prisma AIRS uses more advanced NLP models to interpret semantic meaning of requests, distinguishing genuine complex queries from attempts to get around system prompts or steal sensitive information.
- Layer 3: Behavioral Analysis The system maintains behavioral baselines for every AI agent and flags behaviors that could indicate compromise or abuse.
2. Data Loss Prevention (DLP) at AI Speed
Legacy DLP solutions cannot keep up with the velocity and variety of AI-based requests. Prisma AIRS transforms DLP into the AI era:
# Example: Custom DLP pattern configuration
dlp_config = {
"custom_patterns": [
{
"name": "proprietary_algorithm",
"pattern": r"ALGO-[A-Z]{3}-\d{6}",
"severity": "critical",
"action": "block"
}
],
"ml_classification": {
"model": "financial_document_classifier",
"threshold": 0.85
}
}
server.update_dlp_config(dlp_config)
The system provides:
- 1,000+ pre-defined patterns for PII, PHI, PCI, and industry-specific data
- ML-based document classification that understands context beyond pattern matching
- Real-time policy updates with no service interruption
- Per-tool, per-agent, per-user granular control
3. Intelligent Database Protection
For MCP tools performing database activity, Prisma AIRS provides advanced protection beyond SQL injection prevention:
- Query Analysis Engine
All database queries pass through a multi-step analysis pipeline:
- Syntactic validation: Ensures query structure integrity
- Semantic analysis: Parses query intent and data access patterns
- Permission verification: Evaluates against fine-grained access policies
- Anomaly detection: Identifies anomalous access patterns or amounts of data
- Contextual Access Control Rather than static role-based permissions, Prisma AIRS employs dynamic, context-based access control:
# Example: Context-aware database access policy
access_policy = {
"tool": "customer_database",
"conditions": [
{
"if": "prompt_context.contains('financial_report')",
"then": "allow_read(['transactions', 'accounts'])",
"time_window": "business_hours"
},
{
"if": "prompt_context.contains('customer_support')",
"then": "allow_read(['customers', 'tickets'])",
"exclude_fields": ["ssn", "credit_card"]
}
]
}
4. Toxicity and Content Moderation
AI agents executing in production environments must deliver professional, proper outputs. Prisma AIRS provides sophisticated content moderation:
- Multi-lingual toxicity detection with cultural context sensitivity
- Gradated response system (warn, filter, block) according to seriousness
- Industry-specific topic filtering for individualized requirements
- Bias detection and prevention to ensure fair, ethical AI behavior
Real-World Implementation: Best Practices
1. Progressive Security Implementation
Start with monitoring mode to understand your AI system’s behavior:
# Phase 1: Monitor and baseline
server.set_mode("monitor")
server.enable_analytics(detailed=True)
# Phase 2: Selective enforcement
server.set_mode("enforce",
tools=["database_query", "file_access"],
policies=["dlp", "sql_injection"])
# Phase 3: Full production security
server.set_mode("enforce_all")
2. Custom Policy Development
Leverage Prisma AIRS’ policy engine to create organization-specific security rules:
# Example: Financial services compliance policy
compliance_policy = PolicyEngine.create_policy(
name="sox_compliance",
rules=[
Rule("prevent_financial_data_exposure",
condition="tool.name in ['reporting', 'analytics']",
action="apply_dlp(['financial_records', 'audit_trails'])"),
Rule("enforce_separation_of_duties",
condition="user.role == 'analyst'",
action="restrict_tools(['admin_console', 'user_management'])")
]
)
3. Performance Optimization
Prisma AIRS is designed for minimal latency, but proper configuration ensures optimal performance:
- Local caching of frequently accessed policies
- Asynchronous logging for non-critical events
- Batch processing for high-volume deployments
- Geographic distribution for global deployments
Integration Ecosystem: Beyond Basic Security
Native MCP Host Support
Prisma AIRS MCP Server integrates seamlessly with popular development environments:
- Claude Desktop: Direct stdio transport support
- Cursor/Windsurf: IDE-native security enforcement
- OpenAI Agents: Compatible with custom GPT deployments
- LangChain/LlamaIndex: Framework-level integration
Enterprise Integration
For organizations with existing security infrastructure, Prisma AIRS provides extensive integration capabilities:
# SIEM Integration
server.configure_siem(
provider="splunk",
endpoint="https://splunk.company.com",
events=["security_violations", "dlp_alerts", "anomalies"]
)
# Identity Provider Integration
server.configure_idp(
provider="okta",
tenant="company.okta.com",
attribute_mapping={
"user_role": "okta.user.profile.role",
"department": "okta.user.profile.department"
}
)
The ROI of AI Security: Quantifiable Benefits
1. Risk Reduction
- 99.7% fewer successful prompt injection attacks (based on Unit 42 research)
- 100% blocking of known SQL injection patterns on database queries
- 87% fewer data exposure incidents caused by accidents
2. Operational Effectiveness
- 64% less integration complexity with SDK abstraction
- Zero-downtime policy update and configuration
- Sub-10ms latency introduced for most operations
3. Compliance Streamlining
- Pre-configured compliance templates for SOC 2, HIPAA, GDPR, etc.
- Automated audit trails with cryptographic integrity
- Real-time compliance dashboards for continuous monitoring
Future-Proofing Your AI Infrastructure
As we head towards the future of AI agents, a couple of things are certain:
- More Autonomy: Agents will execute more complex, multi-step actions
- Greater Tool Access: Integration with enterprise systems will become deeper
- Regulatory Scrutiny: AI governance needs will intensify
Conclusion: Security as an Enabler, Not a Barrier
It’s only when organizations feel secure about their security posture that the transformative promise of AI agents can become a reality. Prisma AIRS not only protects against danger—it enables innovation by providing the security platform necessary for far-reaching AI rollouts.
For technical professionals evaluating MCP security solutions, the choice is clear: Prisma AIRS offers the only AI-native, purpose-designed security platform that understands and protects the nuanced dynamics of agent-based systems. It’s not just a matter of preventing breaches—it’s a matter of enabling your AI agents to execute at their highest capability while providing enterprise-class security.
Ready to lock in your AI future? The Prisma AIRS MCP Server is available now in public preview. Head to prisma.pan.dev to get started, or reach out to your Palo Alto Networks rep for an in-depth technical briefing.